Mostly I have done the android app penetration testing on GenyMotion. The problem is that a few apps aren’t working properly lately because of architectural requirements and incompatibility.
Android Virtual Devices (AVD) can be a good alternative, but the images do not support rooting.
So let’s root the AVD to overcome this limitation. The following guide is what I used to setup env on Mac machines.
Start by downloading the SDK or installing Android Studio.
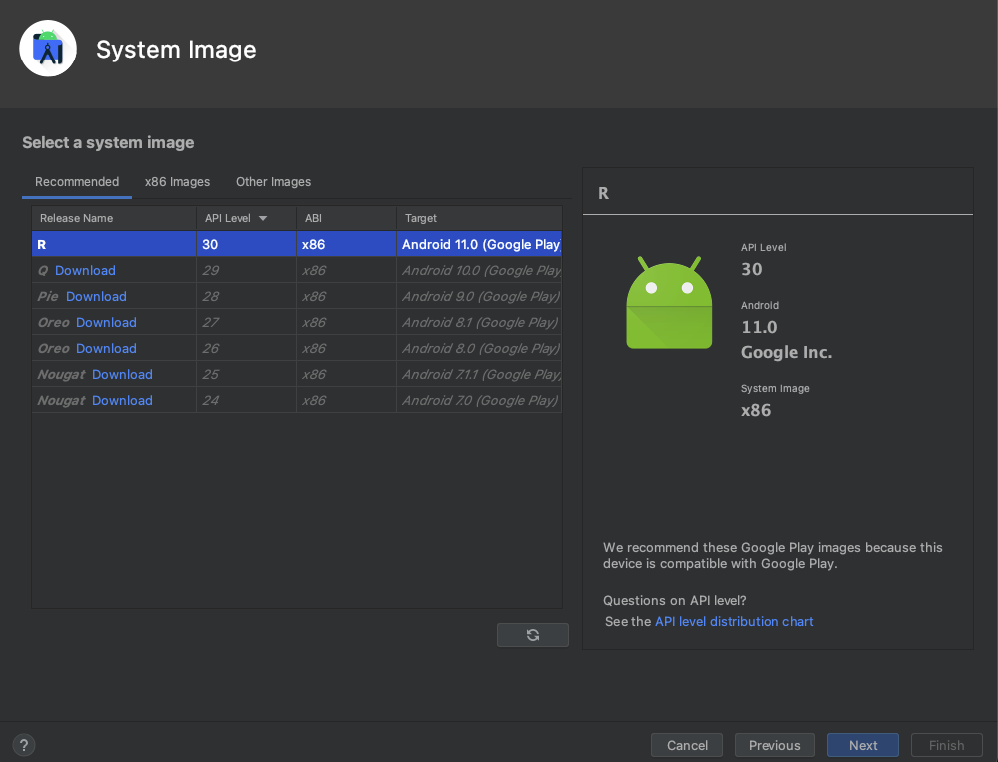
Next, we will create a virtual device. You can choose which System Image you want to download. After booting the device, open the terminal and clone the rootAVD script.
Change the system image (android-xx) accordingly and run:
./rootAVD.sh ~/Library/Android/sdk/system-images/android-30/google_apis/x86/ramdisk.img
./rootAVD.sh InstallApps
Wait for it to finish.
Your phone is now rooted.
adb shell
generic_x86_arm:/ $ su root
generic_x86_arm:/ # whoami
root

In order to intercept traffic and get Frida installed, you need to install a few Magisk modules. Here are some options:
With this setup, you can begin conducting your security assessment.
Thank you and see you next time